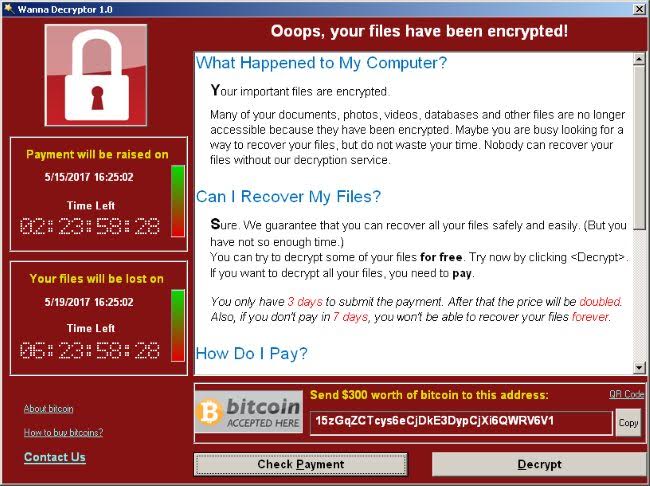
The world’s cybersecurity experts have been quick to comment on the Wannacry ransomware attack that hit the UK’s National Health Service (NHS), Telefonica, FedEx, KPMG and organisations in other countries over the weekend.
Latest reports suggest there is a ‘kill switch’ in the ransomware’s code, which is slowing down its spread.
Experts say that the damage highlights the danger such attacks can do to not only critical healthcare verticals, but to all businesses. And it seems like many are paying the ransom.
The ransomware is a new variant of the Ransom.CryptXXX family. It goes by the names Wanacry, Wannacry, WanaCryt0r, WannaCrypt, WanaDecryptor, or Wana. It is spread through a malicious PDF document that downloads and infects a computer within a business.
It then uses the unpatched SMBv1 vulnerability, also referred to as the MS17-010, to spread through all networked Windows machines.
The cybercriminal group Shadow Brokers is suspected to be behind the attack, which uses a vulnerability originally discovered by the NSA.
We’ve compiled a list of some of the top comments from security experts including LogRhythm, Digital Shadows, Malwarebytes, Tenable Network Security, and MailGuard.
Craig McDonald, CEO, MailGuard:
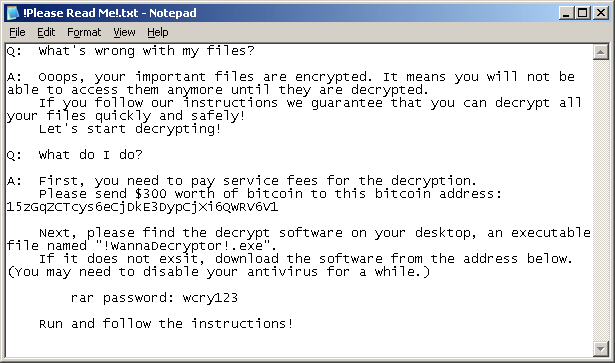
The body of the email contains no information other than an instruction to ‘Please open the attached file’. The ransomware encrypts data on the computers, demanding payments of $300 to $600 to restore access – a relatively small amount, most likely chosen to entice some victims to pay up. The amount doubles if the ransom isn’t paid within 72 hours, and the criminals warn the files will be deleted if the ransom isn’t paid within one week.”
Kasper Lindgaard, senior director of Secunia Research at Flexera Software:
“Frankly, if you wait two months to apply a critical Microsoft patch, you’re doing something wrong. This time, we even had a warning in April that this could very likely happen, so businesses need to wake up and start taking these types of threats and risks seriously. There is simply no excuse.”
Jim Cook, Regional Director – ANZ, Malwarebytes:
“Wana Cryptor is another example of a known, patched vulnerability causing tremendous issues for people and businesses around the world. If possible apply MS17-010 Microsoft patch to all PCs immediately. If you have windows XP machines in your network we recommend disconnecting them until this wave has passed.
“Our research shows the encryption is done with RSA-2048 encryption, which means that it is near impossible to decrypt unless the coders have made an error somewhere.”
Adam Meyers, VP of intelligence, CrowdStrike:
“The attack vector has all the hallmarks of a traditional computer worm. We’ve not seen a large-scale ransomware campaign that uses self-propagating technique at this scale before, which makes it really unique.
“Organisations must act quickly to ensure they are not impacted. Early analysis of the worm is that it is taking advantage of a very recent Microsoft Windows exploit called EternalBlue, which is the enabler for how files get shared. Swift action to patch against this update is critical. Whilst ensuring that back-up data files are disconnected from the core network, as this ransomware has the potential to encrypt back-up files.”
Rick Holland, VP of Strategy, Digital Shadows:
“Keeping up-to-date with ransomware is not easy, there are many variants. Many do get shut down and their encryption cracked, only for another version to spring up – therefore it’s a constant game of constant cat and mouse. Those within the NHS will now be looking to contain the threat. We can only hope that adequate back up measures have been put in place so that vital data can be restored and systems cleaned. Most ransomware locks data rather than steals it – if that is the case here then the threat can be somewhat contained.”
Gerrit Lansing, chief architect, CyberArk:
“We are now seeing instances where attackers can use privileged credentials to find and destroy data backups, which have been typically relied on by organisations to recover from the attack and avoid paying the ransom. Back-ups alone are no longer enough, especially if organisations are exposing privileged credentials to attackers.
This means organisations may have to choose between complete data loss and paying the ransom. Eliminating the attacker’s ability to access administrative credentials to propagate ransomware beyond the initially compromised machine is an essential action to defend against future ransomware attacks and limit damage.”
Gavin Millard, EMEA technical director, Tenable Network Security:
Whilst this isn’t the first time the National Health Service has been hit with Ransomware, it seems like this particular attack has affected more trusts than before. Until the NHS speak publicly about how the ransomware entered their systems and started encrypting crucial files, we can only guess that it was successful due to lax security practices like insufficient patching, poor configuration, and effective filtering of internet communications.
Symantec Security Response:
“Decryption is not available at this time but Symantec is investigating. Symantec does not recommend paying the ransom. Encrypted files should be restored from back-ups where possible.”
Raj Samani and Christiaan Beek, McAfee:
“By remotely gaining control over a victim’s PC with system privileges without any user action, the attacker can spray this malware in the local network by having control over one system inside this network (gaining control over all systems that are not fixed and are affected by this vulnerability), and that one system will spread the ransomware to all vulnerable Windows systems not patched for MS17-010.”
Karl Sigler, Trustwave SpiderLabs:
“Since the exploit capitalises on a vulnerability in the SMB, disabling SMB or blocking SMB at your perimeter firewall is a good proactive measure to stop spreading to vulnerable systems.”
Ryan Kalember, SVP of Cybersecurity Strategy, Proofpoint:
t’s troubling that this worm has proven so problematic for large organisations that are part of critical infrastructure and impact people’s health and wellbeing. We believe it was just a matter of time for an attack like this to occur because this Microsoft exploit was tailor made for malware to spread within an organisation’s network—and ransomware is so profitable for cybercriminals.”
CERT NZ advisory:
“It is also important to ensure that staff are aware of this campaign, and reminded to be extremely vigilant with incoming emails containing links and attachments.”
Michael Bosnar, area vice president ANZ, Ivanti:
“Right now, Australian businesses are opening up for the working week facing the potential impact of the WannaCry ransomware which has hit so many institutions around the world. Organisations should move quickly to patch their systems to avoid being a victim of this attack but also look to implement strategies such as application whitelisting and privilege management to remove the impact of this attack but future attacks.”
Steven Malone, director of security product management at Mimecast:
“The repercussions of Wcry will be with us for the foreseeable future. As less sophisticated attackers take the original malware code and morph it, waves of variants will continue to plague the organisations who are still lagging behind in locking down their systems.”
Nick Savvides, Symantec Security Expert:
“Symantec and Norton protect millions of users in Australia and the telemetry has shown that Australians have been targeted with most attacks being blocked.”
Source: bizEDGE NZ – In-depth: Security experts explain the WannaCry ransomware’s world domination